国密支持
1. 功能说明
使用国密版OpenSSL库来使用SM2、SM3、SM4算法(以下简称为SM234算法)。
SM234算法使用双证书,包括签名证书和加密证书,这是国密支持在证书上的一个特点。
同时,还要求使用的国密版OpenSSL兼容标准OpenSSL。
根据NJet的使用场景,国密支持的场景也细分为Server和反向代理两种场景
2. 指令说明
2.1 ssl_ntls
| Syntax: | ssl_ntls on| off; |
|---|---|
| Default: | — |
| Context: | http,server |
新增 ssl_ntls 指令,用于指定是否使用ntls。
2.2 ssl_certificate
| Syntax: | ssl_certificate file [file]; |
|---|---|
| Default: | — |
| Context: | http,server |
修改 ssl_certificate 指令,可以配置一个或两个证书,当配置两个证书时,前一个是签名证书,后一个是加密证书。
2.3 ssl_certificate_key
| Syntax: | ssl_certificate_key file [file]; |
|---|---|
| Default: | — |
| Context: | http,server |
修改 ssl_certificate_key 指令,可以配置一个或两个秘钥,当配置两个秘钥时,前一个是签名密钥,后一个是加密密钥。
2.4 proxy_ssl_ntls
| Syntax: | proxy_ssl_ntls on| off; |
|---|---|
| Default: | — |
| Context: | http, server, location |
新增 proxy_ssl_ntls 指令,用于代理向后端访问时指定是否使用ntls。
2.5 proxy_ssl_certificate
| Syntax: | proxy_ssl_certificate file [file]; |
|---|---|
| Default: | — |
| Context: | http, server, location |
修改 proxy_ssl_certificate 指令,可以配置一个或两个证书,当配置两个证书时,前一个是签名证书,后一个是加密证书。
2.6 proxy_ssl_certificate_key
| Syntax: | proxy_ssl_certificate_key file [file]; |
|---|---|
| Default: | — |
| Context: | http, server, location |
修改 proxy_ssl_certificate_key 指令,可以配置一个或两个秘钥,当配置两个秘钥时,前一个是签名密钥,后一个是加密密钥。
3 配置说明
NJet作为Server时国密支持需要增加双证书的配置:
server {
listen 443 ssl;
server_name localhost;
ssl_ntls on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers "ECC-SM2-SM4-CBC-SM3:ECDHE-SM2-WITH-SM4-SM3:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA:AES128-GCM-SHA256:AES128-SHA256:AES128-SHA:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:AES256-GCM-SHA384:AES256-SHA256:AES256-SHA:ECDHE-RSA-AES128-SHA256:!aNULL:!eNULL:!RC4:!EXPORT:!DES:!3DES:!MD5:!DSS:!PKS";
ssl_verify_client off;
# 原RSA证书
ssl_certificate /home/certs/cert/sslserver.crt;
ssl_certificate_key /home/certs/cert/sslserver.key;
# 国密支持添加的证书
ssl_certificate certs/SS.crt certs/SE.crt;
ssl_certificate_key certs/SS.key certs/SE.key;
location / {
root html;
index index.html index.htm;
}
}NJet作为proxy时国密支持配置:
server {
listen 8080;
server_name localhost;
# 其他配置,例如:
location / {
proxy_ssl_ntls on;
proxy_ssl_verify on;
proxy_ssl_trusted_certificate certs/CA.crt;
proxy_ssl_certificate certs/CS.crt certs/CE.crt;
proxy_ssl_certificate_key certs/CS.key certs/CE.key;
proxy_ssl_ciphers "ECC-SM2-WITH-SM4-SM3:ECDHE-SM2-WITH-SM4-SM3:RSA";
proxy_pass https://192.168.183.111:443;
}
}4 功能验证
4.1 验证服务器对国密的支持
验证工具为分别为密信浏览器和gmcurl。
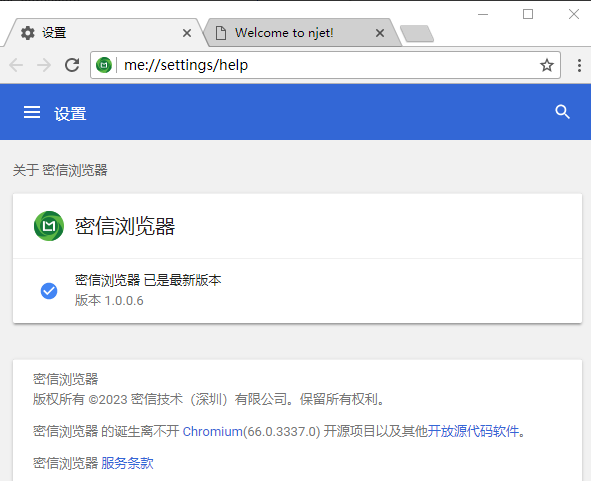
密信浏览器:
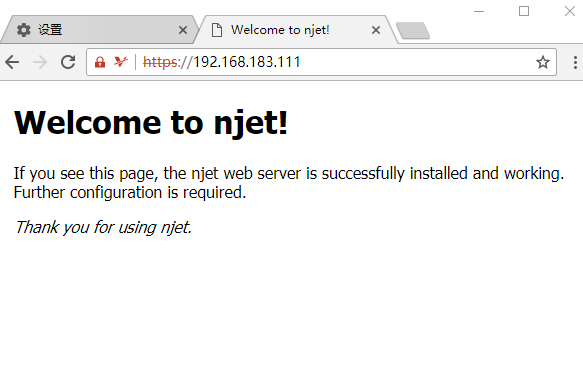
使用密信浏览器访问server:
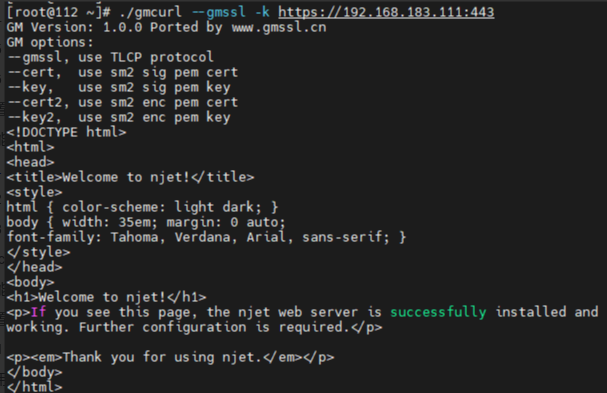
使用gmcurl访问server:
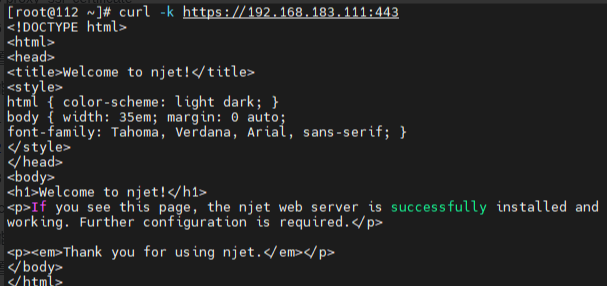
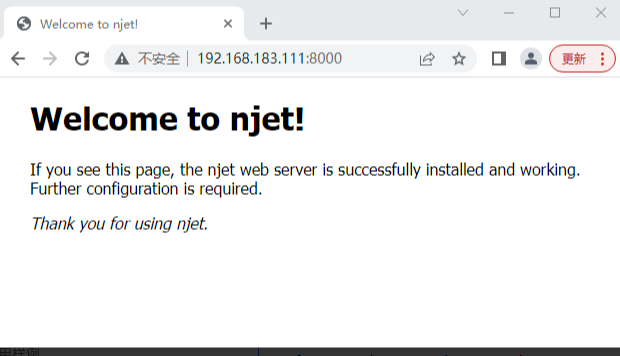
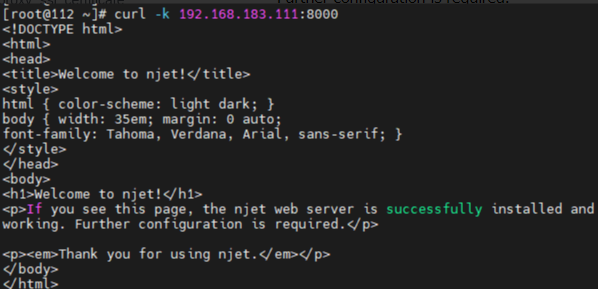
4.2 验证服务器对RSA证书的支持
上节的server的配置中分别指定了RSA证书和国密证书,再验证一下服务器对RSA证书的支持。验证工具为分别为Chrome浏览器和curl。
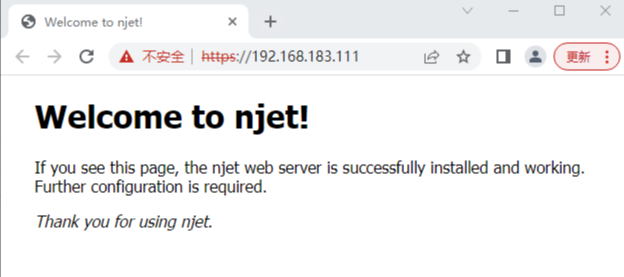
使用Chrome浏览器访问server:
使用curl访问server:
4.3 后端upstream使用国密验证
NJet作反向代理访问后端国密upstream服务器。验证工具为分别为Chrome浏览器和curl。
4.4 国密双向证书校验
njet.conf:
helper broker /etc/njet/modules/njt_helper_broker_module.so conf/mqtt.conf;
helper ctrl /etc/njet/modules/njt_helper_ctrl_module.so conf/ctrl.conf;
cluster_name helper;
node_name node1;
worker_processes auto;
error_log logs/error.log info;
pid logs/njet.pid;
events {
worker_connections 1024;
http {
dyn_kv_conf conf/iot-work.conf;
include mime.types;
include conf.d/*.conf;
#sendfile on;
upstream gmssl {
server 127.0.0.1:4440 max_fails=5 fail_timeout=5;
}
server {
listen 0.0.0.0:4430 ssl;
server_name aaaa;
ssl_ntls on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_verify_client on;
ssl_client_certificate /home/limin/test_guomi/certs/sm2.ca.pem;
ssl_ciphers "ECC-SM2-SM4-CBC-SM3:ECDHE-SM2-WITH-SM4-SM3:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA:AES128-GCM-SHA256:AES128-SHA256:AES128-SHA:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:AES256-GCM-SHA384:AES256-SHA256:AES256-SHA:ECDHE-RSA-AES128-SHA256:!aNULL:!eNULL:!RC4:!EXPORT:!DES:!3DES:!MD5:!DSS:!PKS";
ssl_certificate /home/limin/test_guomi/certs/sm2.aaaa.sig.crt.pem /home/limin/test_guomi/certs/sm2.aaaa.enc.crt.pem;
ssl_certificate_key /home/limin/test_guomi/certs/sm2.aaaa.sig.key.pem /home/limin/test_guomi/certs/sm2.aaaa.enc.key.pem;
location /gmssl {
charset utf-8;
default_type text/html;
return 200 'gmssl:4430 七层负载two';
}
location / {
proxy_ssl_ntls on;
#proxy_ssl_verify on;
#proxy_ssl_trusted_certificate /home/limin/test_guomi/certs/sm2.ca.pem;
proxy_ssl_certificate /home/limin/test_guomi/certs/sm2.aaaa.sig.crt.pem /home/limin/test_guomi/certs/sm2.aaaa.enc.crt.pem;
proxy_ssl_certificate_key /home/limin/test_guomi/certs/sm2.aaaa.sig.key.pem /home/limin/test_guomi/certs/sm2.aaaa.enc.key.pem;
proxy_pass https://gmssl/;
}
}
server {
listen 1430 ssl;
server_name aaaa;
ssl_certificate /home/limin/test_guomi/rsa/rsa..crt.pem;
ssl_certificate_key /home/limin/test_guomi/rsa/rsa..key.pem;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location /test {
proxy_ssl_ntls on;
proxy_pass https://gmssl/;
}
location / {
charset utf-8;
default_type text/html;
return 200 '我是标密';
}
}
server {
listen 0.0.0.0:4440 ssl;
server_name aaaa;
ssl_ntls on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers "ECC-SM2-SM4-CBC-SM3:ECDHE-SM2-WITH-SM4-SM3:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA:AES128-GCM-SHA256:AES128-SHA256:AES128-SHA:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:AES256-GCM-SHA384:AES256-SHA256:AES256-SHA:ECDHE-RSA-AES128-SHA256:!aNULL:!eNULL:!RC4:!EXPORT:!DES:!3DES:!MD5:!DSS:!PKS";
ssl_verify_client on;
ssl_client_certificate /home/limin/test_guomi/certs/sm2.ca.pem;
ssl_certificate /home/limin/test_guomi/certs/sm2.aaaa.sig.crt.pem /home/limin/test_guomi/certs/sm2.aaaa.enc.crt.pem;
ssl_certificate_key /home/limin/test_guomi/certs/sm2.aaaa.sig.key.pem /home/limin/test_guomi/certs/sm2.aaaa.enc.key.pem;
location / {
charset utf-8;
default_type text/html;
return 200 'gmssl:4440 七层负载';
}
}
}客户端带证书访问:
[limin@CDN156 TMZY_NJET]$ gmcurl --gmssl --cert /home/limin/test_guomi/certs/sm2.aaaa.sig.crt.pem --key /home/limin/test_guomi/certs/sm2.aaaa.sig.key.pem --cert2 /home/limin/test_guomi/certs/sm2.aaaa.enc.crt.pem --key2 /home/limin/test_guomi/certs/sm2.aaaa.enc.key.pem --cacert /home/limin/test_guomi/certs/sm2.ca.pem https://aaaa:4430/
GM Version: 1.0.1 Ported by www.gmssl.cn
GM options:
--gmssl, use TLCP protocol
--cert, use sm2 sig pem cert
--key, use sm2 sig pem key
--cert2, use sm2 enc pem cert
--key2, use sm2 enc pem key
gmssl:4440 七层负载