证书吊销列表
1.功能描述
CRL是由CA发布的,包含了所有被撤销的,即不再被信任的数字证书的列表。一个证书可能会被撤销,原因包括但不限于私钥被泄露,证书被误发,或者证书所有者不再需要该证书。
当一个系统在验证一个数字证书的有效性时,它会检查CRL以确保证书没有被撤销。如果证书在CRL中,那么该系统会拒绝与提供该证书的系统建立SSL连接,因为这可能意味着连接的安全性无法得到保证。
因此,SSL和CRL是密切相关的。通过CRL,SSL可以确保在建立的每一个安全连接中,都只使用仍然有效和可信的数字证书。
2.依赖模块
njet.conf:
load_module modules/njt_http_dyn_crl_module.so;njet_ctrl.conf
load_module modules/njt_http_upload_module.so;
load_module modules/njt_http_crl_api_module.so;3.指令说明
ssl_crl 指令可配置证书吊销列表文件
| Syntax: | ssl_crl file; |
|---|---|
| Default: | — |
| Context: | http, server |
Specifies a file with revoked certificates (CRL) in the PEM format used to verify client certificates.
ssl_verify_client: 是否验证开关
| Syntax: | ssl_verify_client on | off | optional | optional_no_ca; |
|---|---|
| Default: | ssl_verify_client off; |
| Context: | http, server |
Enables verification of client certificates. The verification result is stored in the $ssl_client_verify variable.
ssl_client_certificate:CA certificates, 会发送给客户端
| Syntax: | ssl_client_certificate file; |
|---|---|
| Default: | — |
| Context: | http, server |
Specifies a file with trusted CA certificates in the PEM format used to verify client certificates and OCSP responses if ssl_stapling is enabled.
The list of certificates will be sent to clients. If this is not desired, the ssl_trusted_certificate directive can be used.
ssl_trusted_certificate: 可信任CA证书,与ssl_client_certificate 区别是不发送给client
| Syntax: | ssl_trusted_certificate file; |
|---|---|
| Default: | — |
| Context: | http, server |
Specifies a file with trusted CA certificates in the PEM format used to verify client certificates and OCSP responses if ssl_stapling is enabled.
In contrast to the certificate set by ssl_client_certificate, the list of these certificates will not be sent to clients.
4.配置示例
控制面配置示例:
...
#加载文件上传模块,加载后,即可支持/api/v1/upload
load_module modules/njt_http_upload_module.so;
#加载crl吊销证书api模块
load_module modules/njt_http_crl_api_module.so;
...
http {
server {
listen 8081;
client_max_body_size 1G; #文件上传大小配置,默认是1M,如果是大文件,则要配置该指令
#配置api入口
location /api {
dyn_module_api; #开启api
}
#配置上传html,通过该html页面可通过浏览器上传一个文件
location / {
root /root/bug/njet1.0/html;
index upload.html;
}
....
}njet.conf
...
#加载crl证书吊销列表功能模块
load_module modules/njt_http_dyn_crl_module.so;
...
server {
listen 443 ssl;
server_name www.test.com;
ssl_ntls on; #如果是国密证书,则需要配置此开关
proxy_cache_valid any 1d;
expires 1d;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_ciphers AES128-SHA:AES256-SHA:RC4-SHA:DES-CBC3-SHA:RC4-MD5:ECC-SM2-SM4-CBC-SM3:ECDHE-SM2-WITH-SM4-SM3;
ssl_verify_client on; #开启验证客户端证书开关,crl为验证客户端证书吊销列表文件
#RSA证书
ssl_certificate /root/bug/njet1.0/gm/commoncert/certsDir/cert.pem;
ssl_certificate_key /root/bug/njet1.0/gm/commoncert/certsDir/cert-key.pem;
#国密证书
ssl_client_certificate /root/bug/njet1.0/gm/gmcert/more_ca.crt;
ssl_certificate /root/bug/njet1.0/gm/gmcert/server_sign.crt /root/bug/njet1.0/gm/gmcert/server_enc.crt;
ssl_certificate_key /root/bug/njet1.0/gm/gmcert/server_sign.key /root/bug/njet1.0/gm/gmcert/server_enc.key;5.API
5.1API说明
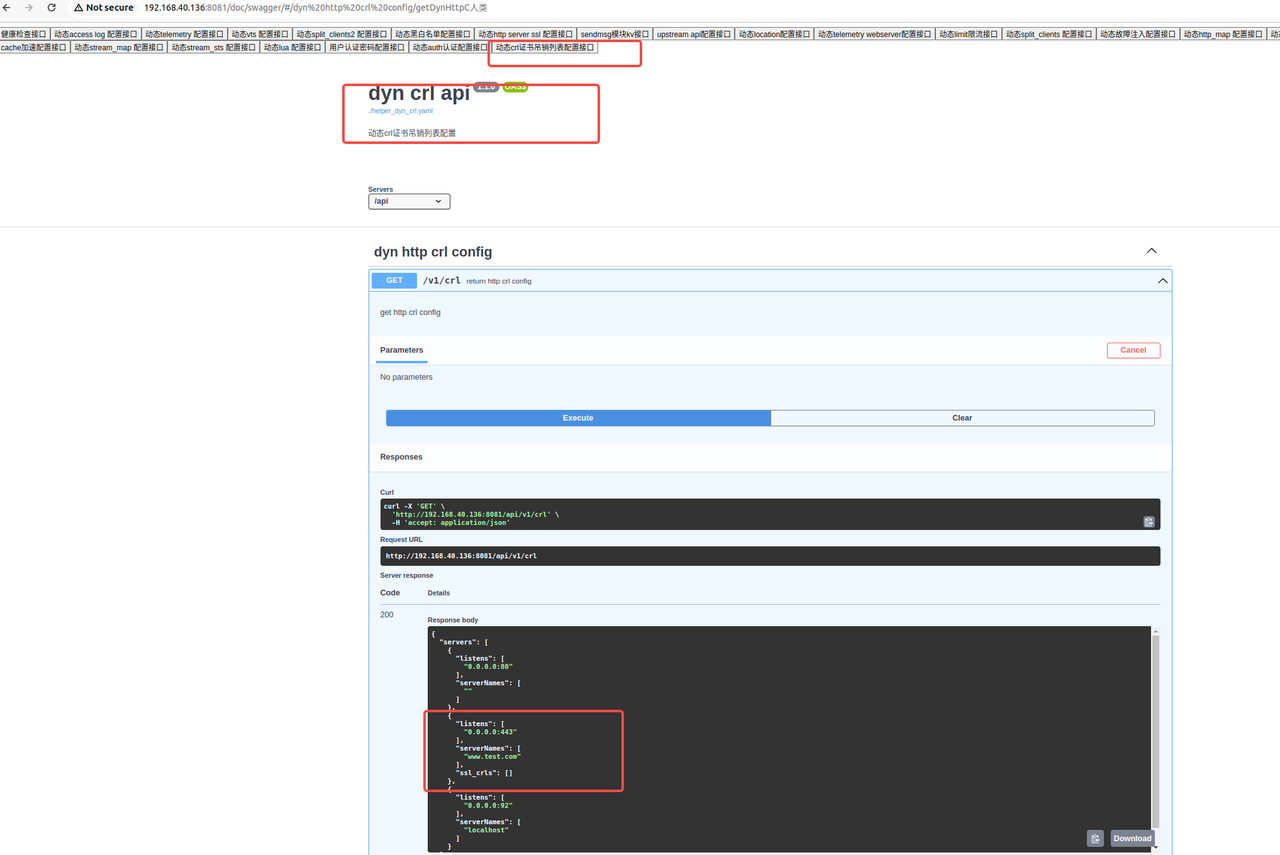
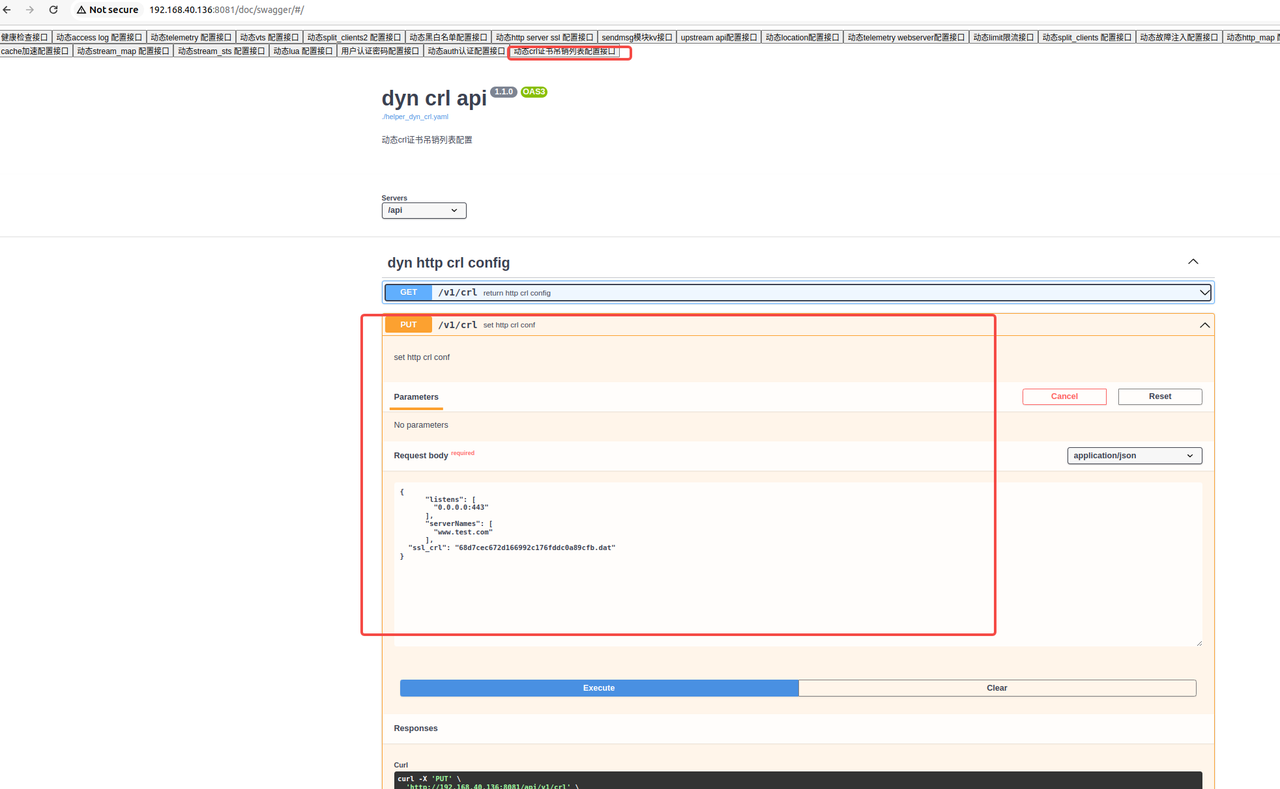
查询接口
curl -X GET http://IP+port/api/v1/crl 修改接口:
curl -X PUT http://IP+port/api/v1/crl 5.2 调用样例
如下为国密证书吊销列表(普通RSA证书吊销列表一致)
初始配置,配置了国密证书,但没有配置crl证书吊销列表,故可正常访问
gmcurl --gmssl -k --cert /root/bug/njet1.0/gm/gmcert/client_sign.crt --key /root/bug/njet1.0/gm/gmcert/client_sign.key --cert2 /root/bug/njet1.0/gm/gmcert/client_enc.crt --key2 /root/bug/njet1.0/gm/gmcert/client_enc.key https://localhost/下面通过文件上传接口,上传crl证书文件到njet服务器
crl01.png
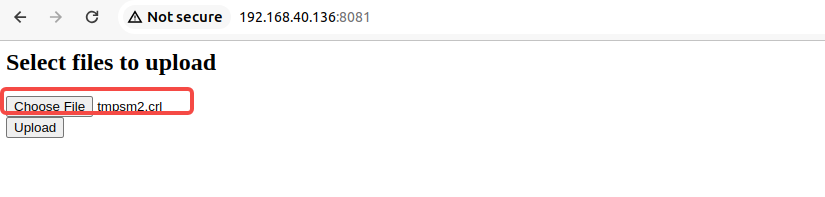

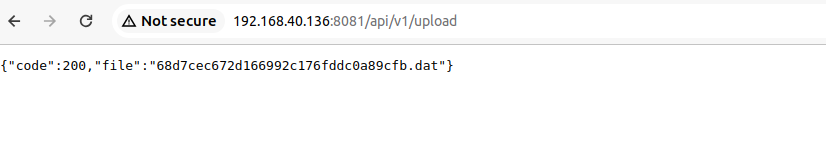
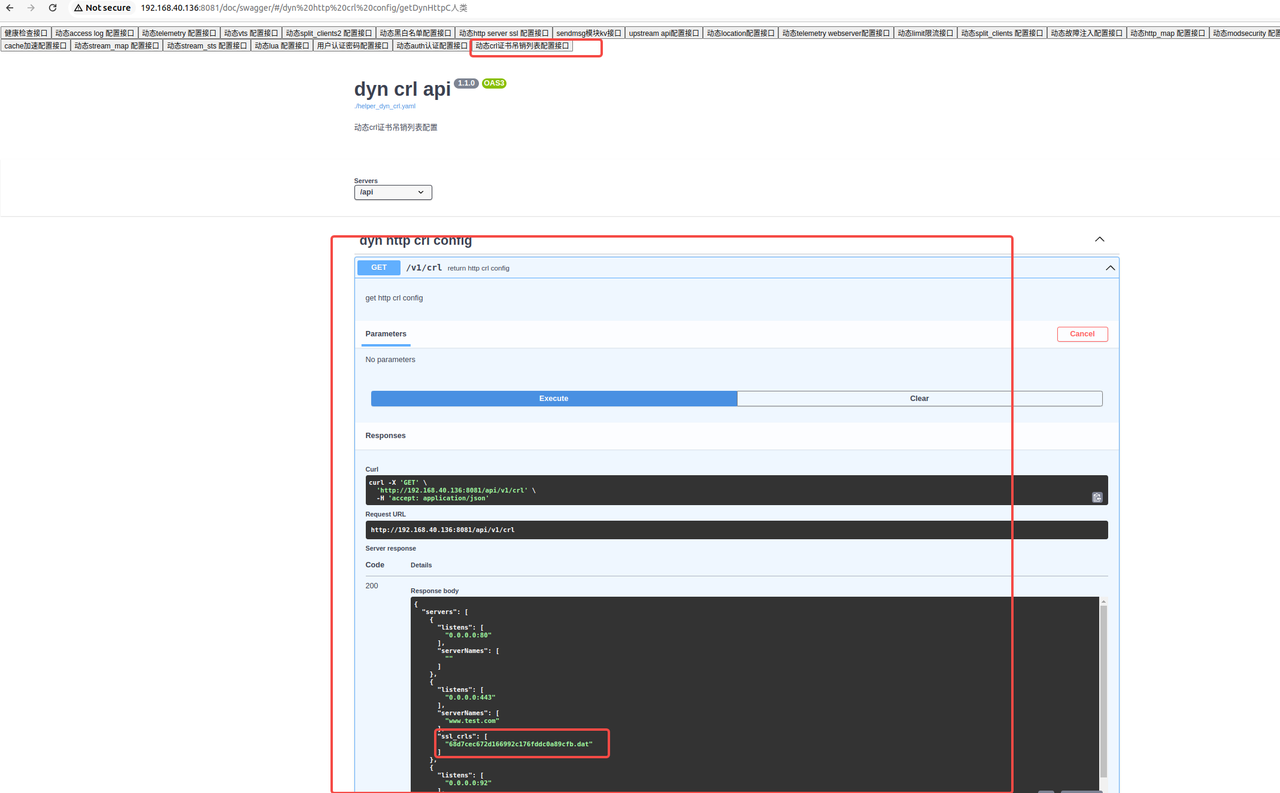
 得到服务器该文件对应的文件名称: 68d7cec672d166992c176fddc0a89cfb.dat
得到服务器该文件对应的文件名称: 68d7cec672d166992c176fddc0a89cfb.dat
通过swagger页面get查询crl配置,初始未配置,所以为空
通过PUT接口配置刚才已经上传的crl文件 68d7cec672d166992c176fddc0a89cfb.dat
[root@localhost gmcert]#
[root@localhost gmcert]# gmcurl --gmssl -k --cert /root/bug/njet1.0/gm/gmcert/client_sign.crt --key /root/bug/njet1.0/gm/gmcert/client_sign.key --cert2 /root/bug/njet1.0/gm/gmcert/client_enc.crt --key2 /root/bug/njet1.0/gm/gmcert/client_enc.key https://localhost/
GM Version: 1.0.2 Ported from curl/7.88.1 by www.gmssl.cn
GM options:
--gmssl, use TLCP protocol
--cert, use sm2 sig pem cert
--key, use sm2 sig pem key
--cert2, use sm2 enc pem cert
--key2, use sm2 enc pem key
<html>
<head><title>400 The SSL certificate error</title></head>
<body>
<center><h1>400 Bad Request</h1></center>
<center>The SSL certificate error</center>
<hr><center>njet/2.1.0</center>
</body>
</html>
[root@localhost gmcert]#